Introduction
Modern enterprises run on data. From cloud platforms and analytics pipelines to AI systems and real-time dashboards, data infrastructure sits at the core of business operations. However, as data environments grow more distributed and complex, cybersecurity risks increase just as rapidly. Many organizations assume that cloud adoption alone guarantees security, yet breaches continue to rise across industries.
Data infrastructure security is no longer a purely technical concern. It is a board-level issue tied to financial loss, regulatory exposure, operational disruption, and reputational damage. Enterprises that fail to secure their data systems place every digital initiative at risk, from analytics and AI to customer experience and compliance.
Understanding Modern Data Infrastructure
Modern data infrastructure includes cloud data warehouses, data lakes, streaming platforms, APIs, analytics tools, and AI workloads. These systems are often spread across multiple cloud providers, regions, and access points. While this architecture improves scalability and performance, it also expands the attack surface.
Each integration, data pipeline, and access layer introduces potential vulnerabilities. Without a unified approach to data infrastructure security, enterprises struggle to maintain visibility and control across their environments.
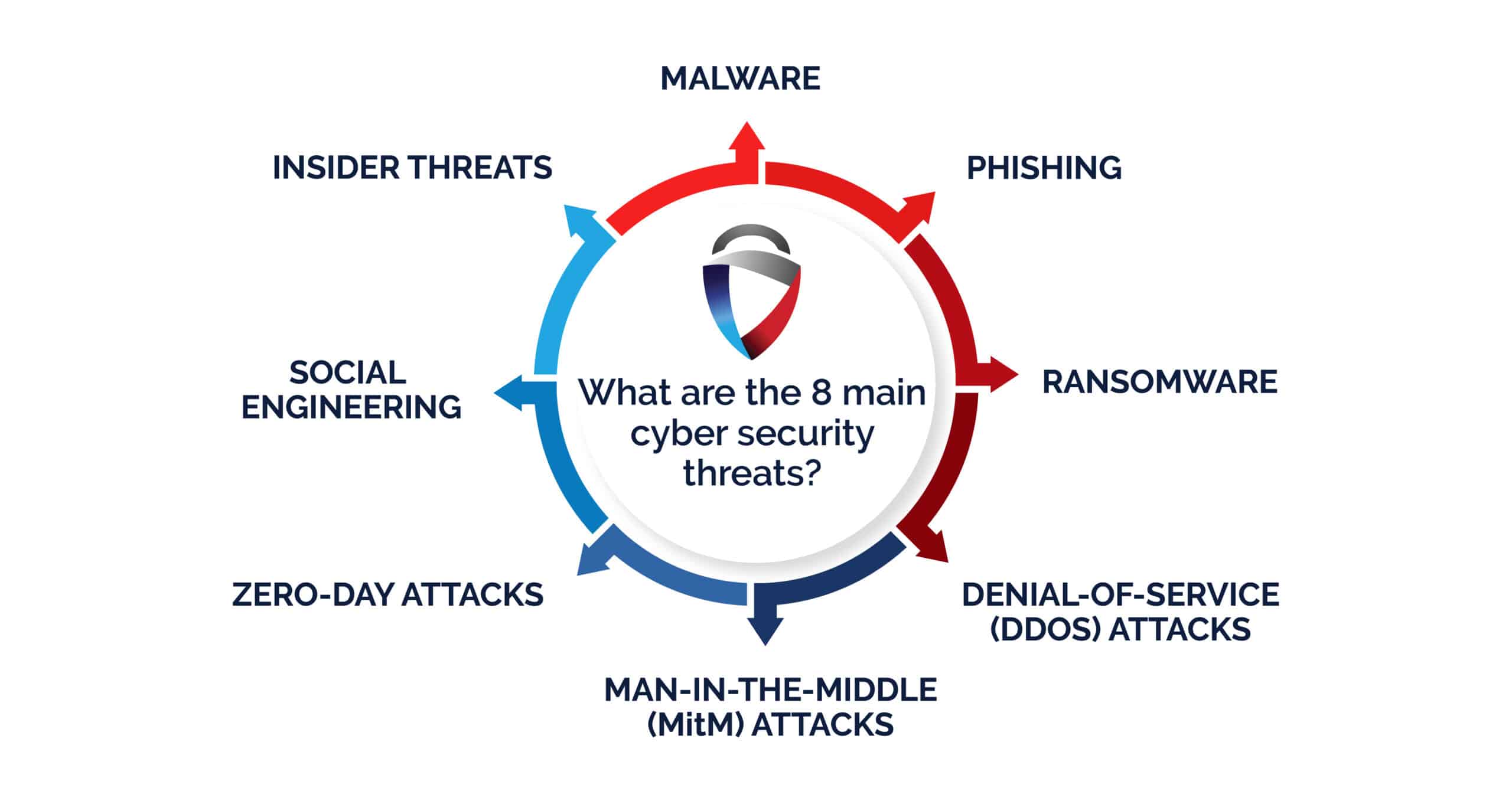
Why Cybersecurity Risks Are Increasing in Data Systems
Cyber threats have evolved alongside data platforms. Attackers now target data pipelines, misconfigured cloud services, and analytics platforms rather than traditional perimeter systems.
Key factors driving increased risk include:
- Rapid cloud adoption without consistent security standards
- Complex multi-cloud and hybrid environments
- Increased use of third-party data tools and APIs
- Growing volumes of sensitive and regulated data
- Expanded access for analytics, AI, and business users
As data becomes more valuable, it becomes a more attractive target.
Major Cybersecurity Risks in Modern Data Systems
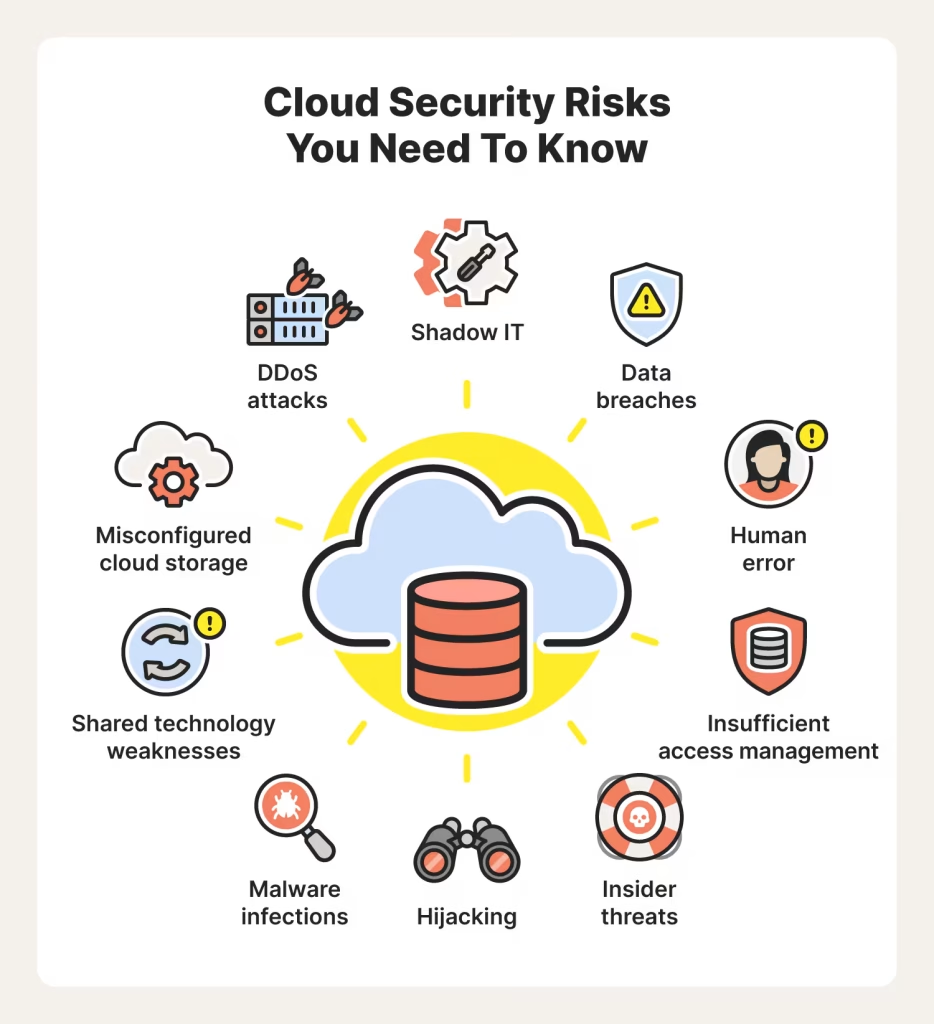
Misconfigured Cloud Resources
Misconfiguration remains one of the leading causes of data breaches. Open storage buckets, overly permissive access roles, and exposed APIs can unintentionally grant attackers access to sensitive data.
Even well-designed architectures become vulnerable when configuration management is inconsistent or poorly monitored.
Weak Identity and Access Controls
Modern data platforms support many users, applications, and automated processes. Without strong identity and access management, organizations risk unauthorized access to critical datasets.
Overprivileged accounts, shared credentials, and lack of role-based access controls significantly increase exposure.
Insecure Data Pipelines
Data pipelines move information across systems continuously. If encryption, authentication, and validation are not enforced end to end, attackers can intercept or manipulate data in transit.
Compromised pipelines undermine analytics accuracy and introduce hidden integrity risks.
Insufficient Monitoring and Detection
Many enterprises lack real-time visibility into data access and usage. Without continuous monitoring, breaches can remain undetected for long periods, increasing impact and recovery costs.
Effective data infrastructure security requires proactive detection rather than reactive response.
Third-Party and Supply Chain Risk
Analytics tools, integration platforms, and external data providers expand functionality but also introduce dependencies. Weak security controls in third-party systems can become entry points for attackers.
The Business Impact of Data Security Failures
Cybersecurity incidents in data systems affect far more than IT operations. They disrupt business continuity and erode trust.
Common consequences include:
- Financial losses from downtime, fines, and remediation
- Regulatory penalties for non-compliance
- Loss of customer and partner confidence
- Delayed analytics and decision-making
- Long-term reputational damage
Strong data infrastructure security protects not just systems, but enterprise credibility.
Building Security into Data Infrastructure Design
Security must be embedded into architecture, not layered on afterward. Enterprises should adopt a security-by-design approach when building or modernizing data platforms.
Implement Zero Trust Principles
Zero trust assumes no user or system is trusted by default. Every access request must be authenticated, authorized, and logged. This model is particularly effective in distributed data environments.
Encrypt Data Everywhere
Encryption should protect data both at rest and in transit. Strong key management ensures sensitive information remains unreadable even if systems are compromised.
Enforce Strong Access Governance
Role-based access, least-privilege policies, and regular access reviews reduce unnecessary exposure. These controls should align with governance and compliance requirements.
Monitor and Audit Continuously
Continuous monitoring of data access, anomalies, and usage patterns allows organizations to detect threats early. Audit trails support investigations and regulatory reporting.
Enterprises strengthening these controls often integrate security into broader governance and quality initiatives such as those supported through https://dataguruanalytics.org/data-quality-validation-solutions.
Data Infrastructure Security and Compliance
Regulatory frameworks increasingly hold organizations accountable for how data is protected and used. Data infrastructure security supports compliance with privacy, financial, and industry regulations by enforcing consistent controls and traceability.
Strong governance models combined with secure infrastructure enable organizations to respond quickly to audits and regulatory inquiries. Many enterprises align security initiatives with strategic advisory support such as https://dataguruanalytics.org/services/research-consultancy/ to ensure both technical and organizational readiness.
Common Mistakes Enterprises Make
Despite awareness, organizations often repeat the same security mistakes:
- Treating security as a one-time project
- Relying solely on cloud provider defaults
- Failing to classify and prioritize sensitive data
- Underestimating insider threats
- Separating security from governance and analytics initiatives
Avoiding these pitfalls requires continuous investment and executive oversight.
Measuring the Effectiveness of Data Infrastructure Security
Security maturity should be measured regularly using clear indicators.
Key metrics include:
- Reduction in unauthorized access incidents
- Faster detection and response times
- Improved audit outcomes
- Consistent enforcement of access policies
- Increased confidence in analytics and reporting
These metrics demonstrate whether security investments are reducing risk and supporting business operations.
Frequently Asked Questions
Are cloud data platforms inherently secure
Cloud platforms provide strong security capabilities, but enterprises are responsible for configuration, access control, and governance.
How does data infrastructure security support analytics and AI
Secure data systems ensure analytics and AI models operate on trusted, untampered data, improving reliability and compliance.
How often should data security controls be reviewed
Security controls should be reviewed continuously, with formal assessments conducted at least annually or after major changes.
Conclusion
Cybersecurity risks in modern data systems are increasing as data environments grow more complex and interconnected. Enterprises that treat data infrastructure security as a strategic priority protect not only their systems but their ability to operate, innovate, and compete. Security is no longer a barrier to analytics and AI. It is the foundation that makes them possible.
Call to Action:
Protect your data at the foundation. Explore expert guidance on securing modern data infrastructure at https://dataguruanalytics.org and build analytics systems designed for resilience, trust, and long-term performance.